
Information Warfare
by u/Case_Newmark
A NEW AGE WAR
For years, Russia has been fighting a war on a new front. Its digital-age propaganda war has shattered the US consciousness, using an army composed of bots to sow its seeds of distrust. The explicit goal has always been “Information Warfare”. Russia, since 2014, has been drowning out real American voices, replacing them with sockpuppet accounts pushing the Kremlin’s agenda. The campaign was a two part process - First, the disinformation campaigns, and later, the hacking and dumping operations.
Russia doesn’t just stop at spreading mistruths already in circulation, or using half baked conspiracy theories. They take the extra step to hack your data, steal your identity for their whims, and use the information they stole against you. Republicans aren’t going to complain. On the contrary, they’ll even argue that it’s irrelevant if Russia spreads that stolen data maliciously. This is Information Warfare in real time, Russia using the information against the Democrats, and Republicans like a fleshlight, to spread discord within our democracy. 20 years ago, this would seem too esoteric, too broad to make any sense. “Sow distrust in democracy”? How could one tear apart the fabric of the greatest democracy on Earth? The very thing that makes America so great in the first place? Turns out, you do so one thread at a time.
It requires patience. Russia has been planting the seeds of their digital offensive since at least 2014. Their hacks of the Democratic National Committee (DNC) and the Democratic Congressional Campaign Committee (DCCC) in 2016 acted as a signal to the rest of the world. Russia was writing the new rules of propaganda distribution and leading the charge on the digital front. All while slowly, patiently, chipping away at the world’s predominant power.
The Mueller Report outlines the Russian plot since its conception.
In mid 2013, Russia founded the IRA, or Internet Research Agency; a vague entity with the express goal of spreading foreign influence campaigns with the blessing of the Russian government, and assistance of the Russian Intelligence service, the GRU. While the goal initially was to simply undermine the US election system, the mission evolved into an effort to disparage the 2016 presidential campaign of Hillary Clinton, and to promote Donald Trump’s campaign. The Russian Government used the IRA to establish the two-part system Russia would use to influence the US democratic system.
First, the IRA carried out a social media campaign that favored presidential candidate Donald J. Trump and disparaged presidential candidate Hillary Clinton.
Second, Active GRU officers employed by the IRA conducted computer-intrusion operations against entities, employees, and volunteers working on the Clinton Campaign. Using that hacked data, Russia would then strategically release stolen documents at times that would harm the Democrats the most.
Due to the Trump Administration’s efforts to obstruct the investigation, as well as evidence destroyed by the IRA, some actions and events will lack direct evidence or have conflicting evidence. In some instances, evidence was redacted or censored. The report clearly states, “That the investigation did not establish particular facts does not mean there was no evidence of those facts.”
Invisible Invaders
The IRA began operations targeting the United States by at least 2014, creating a “Translator Department”, which focused solely on influence operations in the United States. IRA employees Anna Vladislavovna Bogacheva and Aleksandra Yuryevna Krylova travelled to the United States on June 14th, 2016, on an intel operation to obtain information and photographs to use in their social media posts.
Using fake U.S. personas, the IRA operated social media accounts designed to attract U.S. audiences. These accounts, which focused on divisive U.S. political and social issues, would claim to be controlled by U.S. activists. Over time, these social media accounts grew and grew, and began influencing real US citizens.
The IRA would steal identities or operate under false ones to enable the logistics of their plan. They used stolen birthdates, socials, and other sensitive information to pass as regular Americans, and using these, opened several bank and paypal accounts.
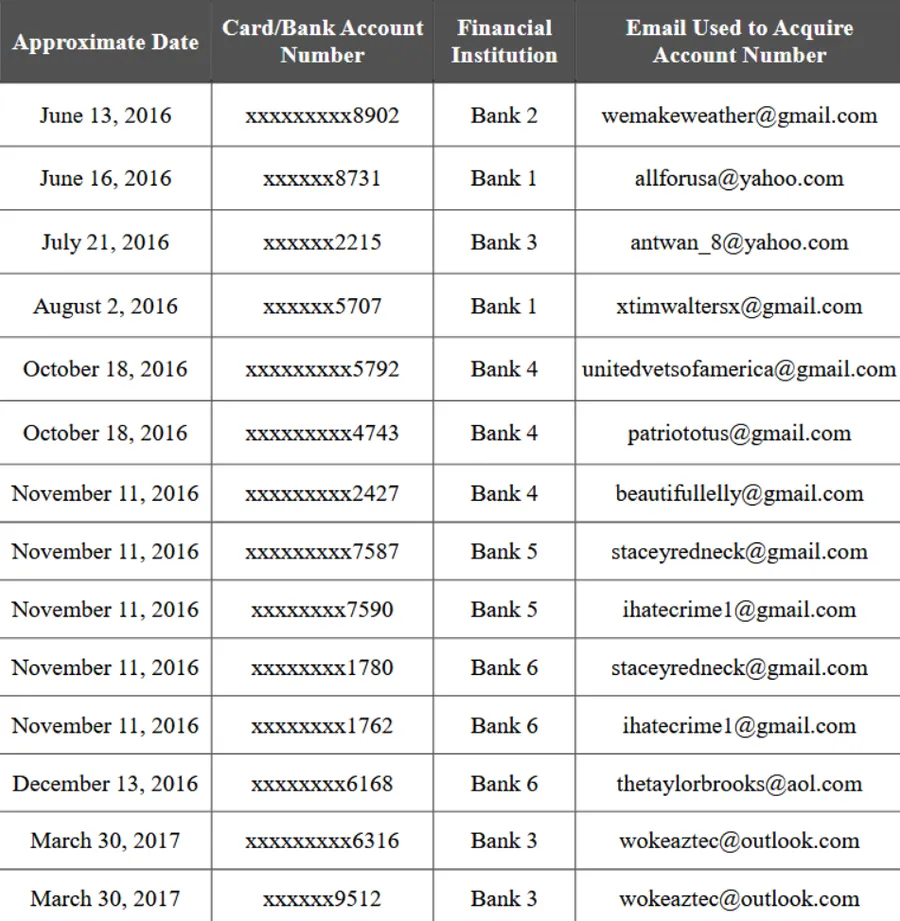
Chart from Page 33 of IRA Indictment.
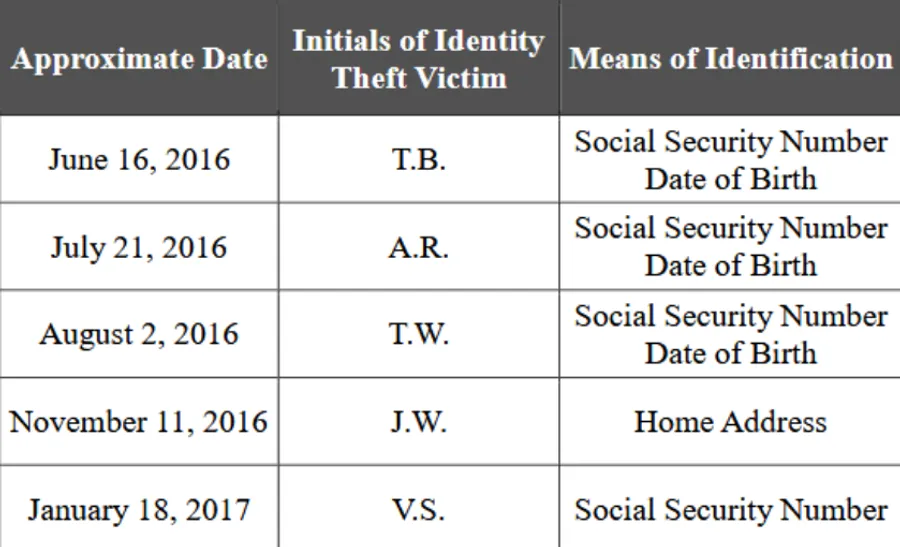
Chart from Page 32 of IRA Indictment.
These operations were enabled by GRU officers who worked alongside the IRA to hack and steal sensitive data. Among the most notable figures were Aleksey Lukashev, the hacker responsible for breaching John Podesta’s emails; Ivan Yermakov, who provided key technical assistance to Lukashev; and Viktor Netyshko, who served as a ringleader of the broader hacking campaign.
The GRU also operated a number of bitcoin mining operations, used to help fund the infrastructure needed to conduct the operations. The funds used to pay for the dcleaks.com domain originated from an account at an online cryptocurrency service that the GRU used to fund the lease of a virtual private server, registered with the operational email account [email protected]. That same dirbinsaabol email account was also used to register the @john356gh URL-shortening account that would later be used by Lukashev to “spearphish” Podesta.
To finance and support these operations, the operatives would purchase and exploit stolen American identities and financial accounts. U.S. citizen Richard Pinedo pleaded guilty to this, admitting selling the IRA hundreds of fraudulently obtained U.S. bank account numbers. By using these stolen identities, IRA employees were able to open and control accounts on U.S. financial networks (including online payment systems) while posing as ordinary Americans. Mueller explains that Pinedo’s scheme “allowed the IRA members to anonymously access a financial network” and transact with U.S. persons and companies, allowing them to operate and appear like domestic institutions.
Later, the officers would use the same pool of bitcoin funds to purchase a virtual private network ("VPN") account and to lease a server in Malaysia. Then, around June 2016, the IRA used the Malaysian server to host the dcleaks.com website. They would later use that same server and VPN to log into the Twitter account “@GUCCIFER2.0”. GRU officers also opened the VPN account from the same server that was also used to register spearphishing domains and sites to hack the DCCC and DNC.
Crossing the threshold
As their influence grew, so did the scope of the Translator department. Thus, the department was subdivided to increase operational efficiency. The responsibilities ranged from ops across different social media sites (Twitter, Facebook, Tumblr, etc), to analytics, graphics, and IT. Dozens of “Specialists” - the term coined for the operators of the personas and sites - were employed to subtly invade our public spaces, and infect them with disinformation and apathy. Here are some examples of the types of political ads they would purchase, and then spread to achieve this goal.
“You know, a great number of black people support us, saying that #HillaryClintonIsNotMyPresident”
“I say no to Hillary Clinton / I say no to manipulation”
“Donald wants to defeat terrorism . . . Hillary wants to sponsor it”
“Hillary Clinton has already committed voter fraud during the Democrat Iowa
Caucus.”
They started small. They would pretend to be real US citizens, using names like “Kate S. Milton” or @jenn_abrams (a false Virginian Trump supporter with 70,000 followers), but quickly decided to make accounts falsely affiliated with real political parties, like the infamous @Ten_GOP account, which claimed to be associated with the Tennessee GOP. It was a two step process, with the main accounts posting original disinformation content, and a network of automated accounts to follow and amplify the message. With enough bots yapping about whatever the IRA wanted them to yap about, their ideas began to poke into the public consciousness. This led to figures with close ties to the Trump Campaign, such as Micheal Flynn, Roger Stone, and Sean Hannity, promoting IRA-made content.
Russia didn’t just impersonate republicans, as shown with Tumblr accounts like @ghettablasta or with the Twitter account @Blacktivist. Black Lives Matter was at the forefront of the American consciousness, and GRU Officers like Ivan Yermakov used that to their advantage. They would intentionally stoke racial flames, in an attempt to get PoC voters to think one thing; “Both parties suck, why should I vote?”
Through these sites/personas, the IRA would organize rallies, talk with real US citizens, and leak hacked materials, using the established influence to amplify the hack and dump operations.
By February 2016, a redacted internal IRA document stated “Main Idea: Use any opportunity to criticize Hillary [Clinton] and the rest (except Sanders and Trump - We support them). Later, in the IRA-controlled Facebook group "Secured Borders," the author criticized the "lower number of posts dedicated to criticizing Hillary Clinton" and reminded the Facebook specialist that "it is imperative to intensify criticizing Hillary Clinton."

Example of a propaganda post on Tumblr made by an IRA-Controlled account. @Ghettablasta changed their name to @PostingWhileBlack.
The IRA’s influence did not stop at disinformation websites. They organized rallies, some in empty parks, but others in packed gyms. For example, on May 31st, 2016, IRA persona “Matt Skiber” began messaging dozens of Pro-Trump accounts to attempt to organize a “pro-Trump rally near Trump Tower”.
The IRA had developed a solid system for organizing the rallies. First, they would use a pre-existing persona to announce the rally. Then, the IRA would send mass DMs to their followers, asking them to attend the rally. Out of the pool of people who would respond to the DM, the IRA would pick a US coordinator. They would tell the real US citizen that they could not attend the rally due to a health concern or because they were not in the same state. When the coordinator agreed, the IRA would message media outlets and direct them to the coordinator. After the rally is over, they would post pictures and videos across their feeds, to help amplify the next rally. This system was used again and again, and had particular success with coordinator Susie Wiles, and the “Florida goes Trump” rallies.
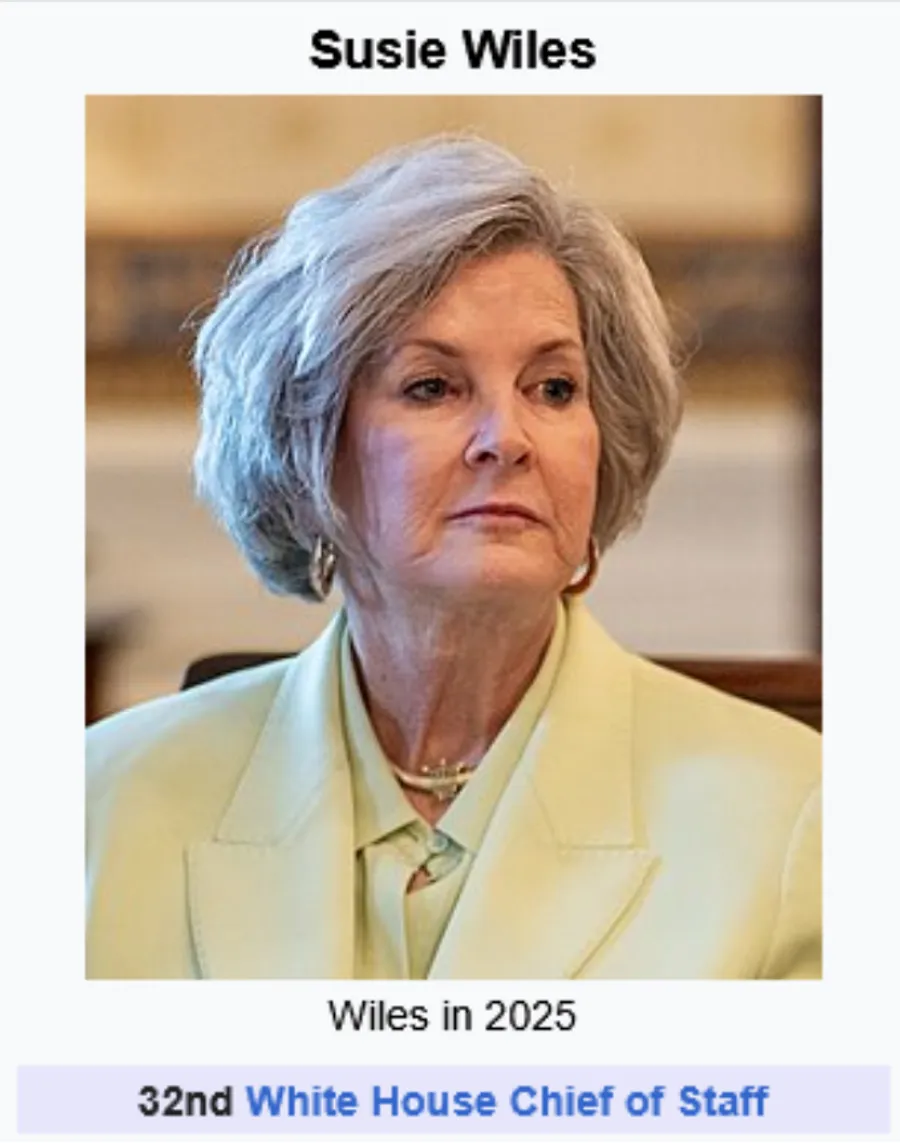
Susie was a diehard Trumpie, and on August 15th, 2016, she emailed one of the IRA’s personas, offering her help to organize the Florida rallies. Susie insisted that her staff had not wittingly cooperated with Russians, the DOJ backs up this claim. Notably, though, a few days after the infamous Trump Tower meeting, Wiles' husband Lanny Wiles arranged for Natalia Veselnitskaya, the Russian lawyer present at the meeting, to get a prominent seat at the Magnitsky sanctions hearing. Lanny claimed he went early to scout out the seat, and was there at the request of Rinat Akhmetshin (The other Russian spy present at the meeting), with whom he was working as a consultant on the sanctions issue. Veselnitskaya would later be indicted for obstruction of justice, and Akhmetshin would be subject to a complaint for failing to disclose himself as a foreign agent. Politico would report that Lanny Wiles had some kind of financial role in Akhmetshin’s anti-Magnitsky act lobbying. Susie Wiles would later become involved with Trump’s handling of classified documents in 2021, after Trump showed her a classified map.
Susie Wiles is now the White House Chief of Staff. Loyalty rewarded. Wiles’ story provides a good outline for many of the stories and evidence in the report. No direct ties or linking of evidence to Russia, but suspiciously close relations, one layer removed from Trump himself. People like Susie were prime targets for the IRA, people either willing to play the fool, or actually foolish enough to fall for these schemes. The Susie Wiles of the world are the ones helping burn down our democracy, at the behest of Russia.
The rallies were not possible without the help of corrupt individuals like Wiles. The logistics would have been too difficult to overcome remotely. How would Russian hackers hand out signs in America? It should be noted that the investigation did not find evidence that coordinators knew the true nature of the IRA personas behind the organizing.
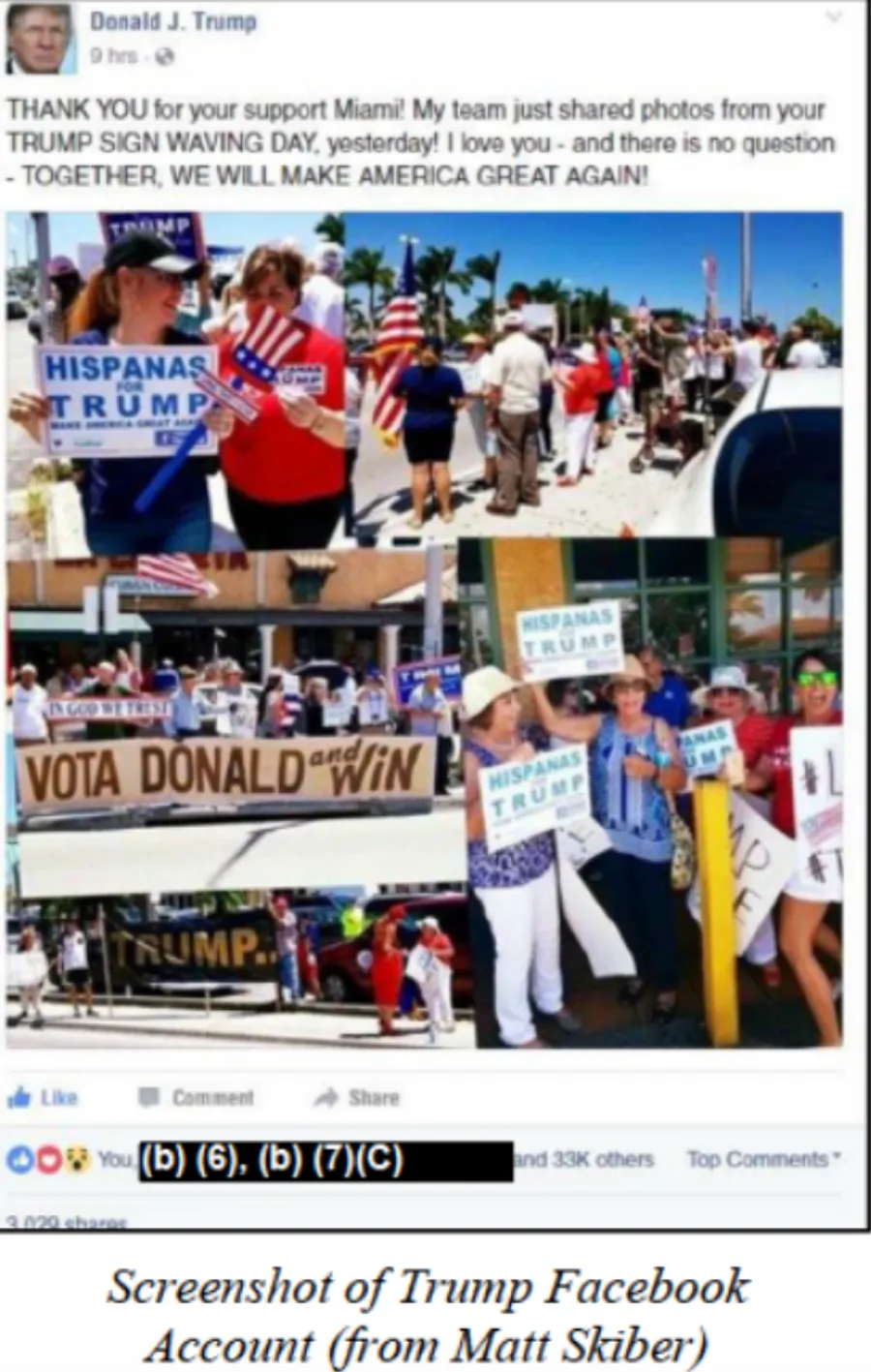
From June 2016 to the end of the campaign, nearly all the rallies focused on the election. The rallies would almost always promote the Trump Campaign, and oppose Clinton’s. These included around 3 rallies in New York and a series of pro-Trump rallies in Florida called “Florida goes Trump”. These rallies, particularly the one in Miami organized in part by Wiles, were posted to Trump’s personal Facebook account.
The IRA was ecstatic about Trump noticing the Miami rallies, all enabled by Wiles. On August 23, 2016, the "Matt Skiber" persona sent a message on Facebook to a U.S.Tea Party activist. "Mr. Trump posted about our event in Miami! This is great!"
From Page 34 of the Mueller Report
Ghosts in the System
In March 2016, GRU units working in conjunction with the IRA hacked Clinton Campaign Chairman John Podesta. Then, in April 2016, they hacked the Democratic Congressional Campaign Committee (DCCC) and the DNC. They targeted sensitive documents, and in all, harvested hundreds of thousands of them. Once they had their hands on the compromised data, they opened the website DCleaks.com, then switching to the moniker Guccifer2.0. Finally, they began releasing the bulk of the files on wikileaks. To accomplish this, the Russian government assigned two Units to the IRA campaign, Units 26165 and 74455.
Unit 26165 is a cyber unit, dedicated to targeting military, political, governmental, and non-governmental organizations outside of Russia. This unit - which we will shorten to 261 for the sake of clarity - had multiple departments. One sub-division made malware, like Russia’s X-Agent and X-Tunnel, which were instrumental to hacking the DNC and DCCC.. Another conducted large-scale spearphishing operations. There was also a sub-division that had a large-scale bitcoin mining operation, which they would use to secure the infrastructure necessary for their hacking operations. This unit was the one primarily responsible for hacking both the DCCC and the DNC.
Unit 74455 is a related unit with multiple cyber departments. 744 helped leak documents stolen by 261, and promoted the releases alongside the anti-Clinton propaganda made by the IRA. 744 also hacked several state board of elections (SBOE) and secretaries of state.
To accomplish the hack, GRU officers sent hundreds of spearphishing emails to employees of the Clinton Campaign, starting on March 10th. They cast a huge phishing net, and caught a few employees, but it wasn’t until the 19th that they caught their biggest phish yet.
Using gmail account @john356gh, Lukashev altered his email to appear as a security notification from Google to change passwords. Fooled (and 67 years old), Podesta clicked the link, and changed passwords. From here, they began to harvest their schools of phishes.
On March 21st, Lukashev used X-Tunnel to steal thousands of emails from Podesta and other staffers.
On April 12th, Lukashev and Ivan Yermakov got into the DCCC’s network using the credentials of a DCCC employee speared about a week earlier. 6 days after that, on April 18th, Lukashev and Yermakov got into the DNC through a VPN connection between both networks. From then until June 8th, they managed to infect over 30 computers on the DNC network, and 29 DCCC computers.
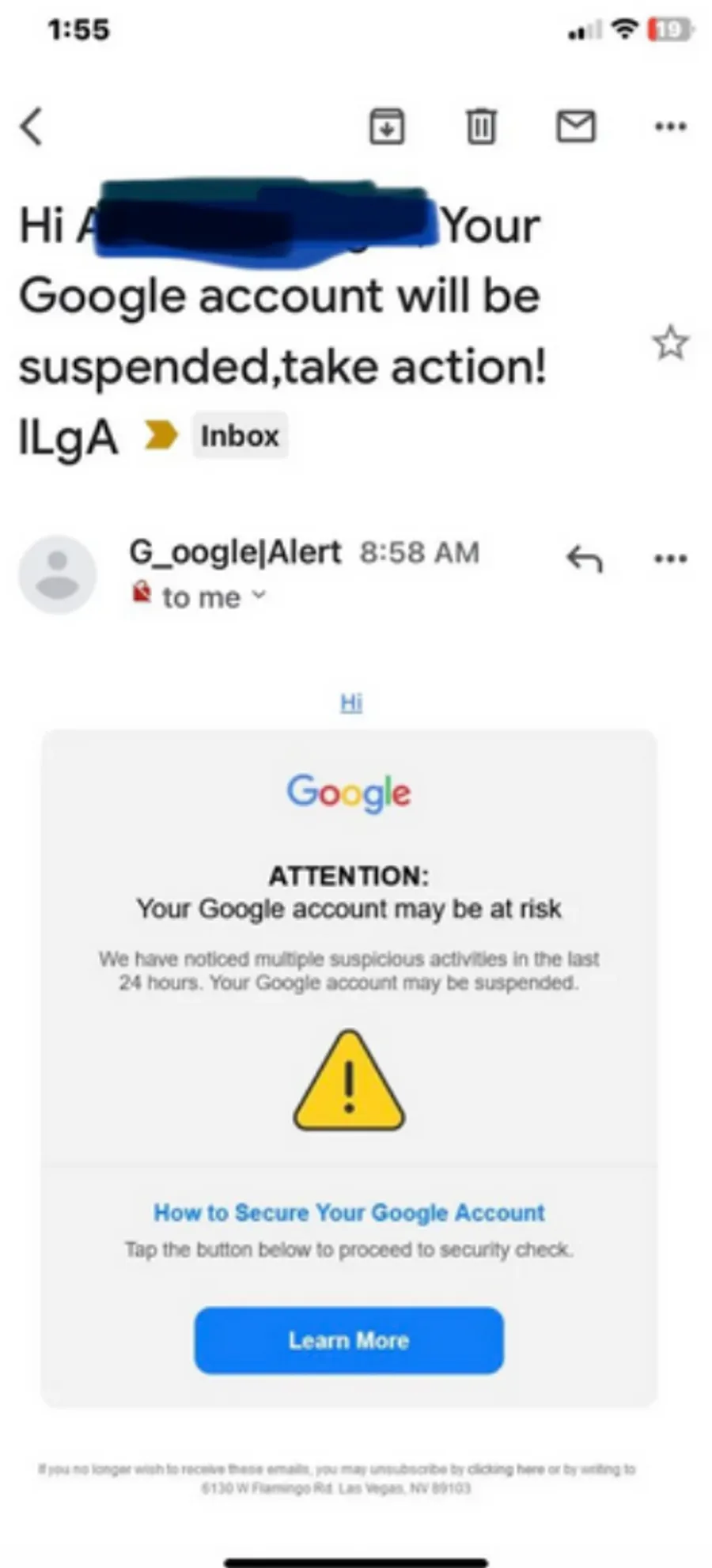
Example of a fake Google security notification
Source
Even as CrowdStrike and American intelligence announced its discovery of the hacks, the GRU continued on targeting and hacking democrats, and later, SBOE.
In July, Trump publicly asks Russia to “find” more of Hillary’s emails, saying
Within 5 hours of this statement, GRU Officers for the first time targeted Clinton’s personal office. 261 created and sent 15 malicious links to members of her staff. It is unclear how the GRU had access to these emails, as they weren’t public.
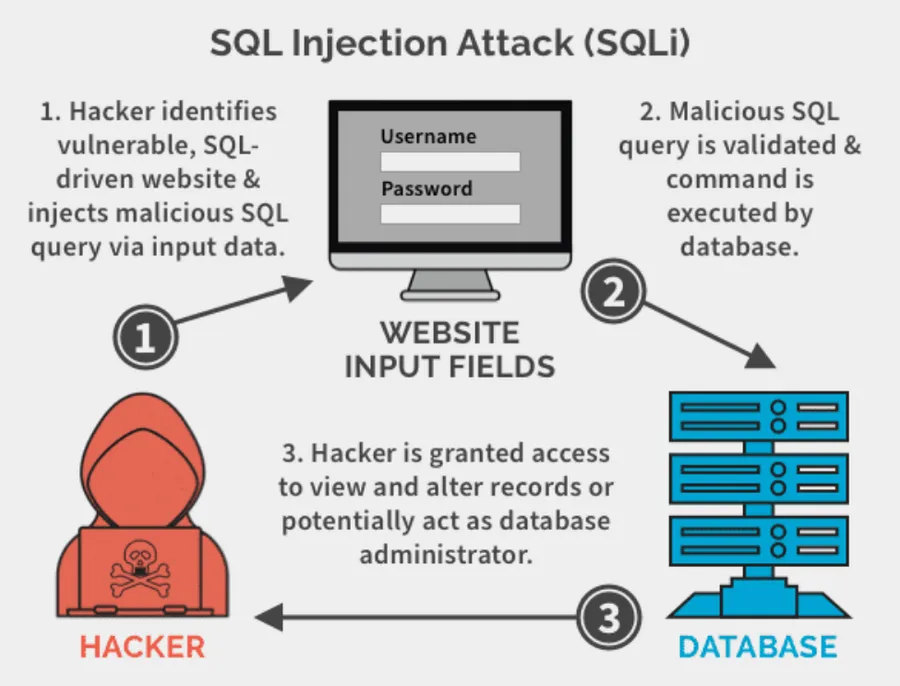
In addition to targeting individuals in Clinton’s staff, they also began targeting election officials. The victims encompassed U.S. state and local organizations including SBOEs, secretaries of state, and county governments, as well as the individuals who worked for these entities. Using SQL Injections, (A string of malicious code that was sent to the state or local website in order to run commands) they compromised SBOEs like Illinois’, then gained access to millions of registered Illinois voters, including PII and partial socials.
They would also send spearphishing emails to companies producing voting technology and to election officials. In November 2016, the GRU sent spearphishing emails to more than 120 email accounts used by Florida county officials responsible for administering the 2016 U.S. election.
The emails contained a Trojan virus embedded in a Word document, which allowed GRU Officers into the computers, which according to the FBI, was to gain access to county networks.
These hacks could not be accomplished without the help of X-Agent and X-Tunnel. X-Agent was a multi-function hacking tool that allowed Unit 261 to take screenshots, log keystrokes, and otherwise gather information on infected PCs. X-Tunnel created an encrypted connection between the Victim and the Hacker’s computer, and allowed for large-scale data transfers.
To cover their tracks while they stole the data, Unit 261 used multiple proxies to transfer the data. First, infected PCs would transmit data to a set of computers known as the “Middle Server”. Then this would then go to another set of computers known as the “AMS Panel”, housed in Arizona.
It was through the AMS panel that the GRU was able to operate the viruses. The panel stored thousands of files, including passwords, internal communications, banking info, and sensitive personal information.
In total, both units stole hundreds of thousands of documents, including critical information regarding the 2016 elections. They stole fundraising data, oppo research, and internal strategy docs, among other things.
On April 14th, GRU officers download rar.exe (a service used to compile data) onto the DCCC server, and the next day search for files including “Trump”, “Clinton”, “Cruz”, and “Benghazi Investigations”, as well as opposition research done by the Clinton campaign into candidate Trump. Then, on the 25th, they compress an unknown amount of files and X-Tunnel’d them out. In total, they stole around 70 gigabytes of data from the DCCC server this way. These files were later released by Wikileaks in July 2016.
October Surprises
The GRU created two personas, dcleaks.com, and guccifer2.0, to initially dispense the stolen data, but later used Wikileaks to increase their reach.
The dcleaks domain was first registered on April 19th, after Unit 261 failed to secure the domain electionleaks.com. The site, of which an archived version still exists today, divided the leaks into sections by person or by topic. Alongside the site, a twitter account was made, @dcleaks_, and a facebook account was made, DCLeaks.
To control the timing of the releases, some sections were password protected until the release date, when it was made public.
Starting on June 8th, the GRU begins posting stolen emails and documents onto the site. Many of these emails came from personal email accounts, like google or microsoft accounts, and not from DNC or DCCC computer networks. These documents included Personal Identifying Information, financial information, fundraising files, and internal communications between Clinton Campaign staff.
GRU Officers also used the accounts to communicate directly with reporters and political pundits, offering certain people early access to leaked materials.
On June 14th, CrowdStrike, along with the DNC, announced the discovery of the Russian hack by State-Sponsored actors. In response, the officers searched on a Moscow based server for the following terms:
"some hundred sheets" , "some hundreds of sheets" , “dcleaks” , illuminati , широко известный перевод [Translation: “widely known”], "worldwide known" , "think twice about" , and "company's competence".
On June 15th, GRU officers created the Guccifer2.0 persona on a WordPress, with the title, "DNC's servers hacked by a lone hacker”.
“Worldwide known cyber security company CrowdStrike announced that the Democratic National Committee (DNC) servers had been hacked by "sophisticated" hacker groups. I'm very pleased the company appreciated my skills so highly))) [. . .] Here are just a few docs from many thousands I extracted when hacking into DNC's network. [. . .] Some hundred sheets! This's a serious case, isn't it? [...] I guess CrowdStrike’s customers should think twice about company's competence. F[***] the Illuminati and their conspiracies!!!!!!!!! F[***] CrowdStrike!!!!!!!!!”
The next day, they began releasing stolen documents on WordPress, and continued until October 18th, 2016.
The GRU began contacting real people using the Guccifer2.0 persona as well. On June 27th, Guccifer sent an email to The Smoking Gun, offering "exclusive
access to some leaked emails linked to Hillary Clinton's staff”. Later, the GRU would send a reporter from the Gun a link containing an archive of emails stolen by 261.
In another instance, Guccifer received a request from a candidate for US congress, Harold "Russell" Taub, for files on his opponent. They obliged.

Taub with John Bolton
In order to increase range and access to the hacked materials, the GRU transferred many of the stolen materials to Wikileaks for distribution. The officers used both Guccifer2.0 and DCLeaks to communicate with Wikileaks. Both the GRU and Wikileaks took steps to hide and destroy evidence of communications, limiting the scope of the evidence.
Wikileaks founder Julian Assange had voiced strong opposition to candidate Clinton’s campaign. On November 15th, Assange messaged other members of Wikileaks, saying
“We believe it would be much better for GOP to win…. With Hillary in charge, GOP will be pushing for her worst qualities... She’s a bright, well-connected, sadistic sociopath.”
On March 16th, 2016, WikiLeaks released a searchable archive of approximately 30,000 Clinton emails that had been obtained through FOIA litigation. A web designer who worked on the archive DMed another worker on Twitter, saying,
“[W]e want this repository to become “the place” to search for background on hillary’s
plotting at the state department during 2009-2013 … Firstly because its useful and will annoy Hillary, but secondly … because eit [sic] may en[]courage people to send us even more important leaks.”
Then, on July 6th, Wikileaks DMed the Guccifer2.0 twitter account, saying,
“if you have anything hillary related we want it in the next tweo [sic] days prefable [sic] because the DNC is approaching and she will solidify bernie supporters behind her after.”
This clearly shows that Assange knowingly released the files to harm Clinton’s campaign, not just as a neutral third party hoster of leaked materials.
WikiLeaks then explained,
“we think trump has only a 25% chance of winning against hillary . . . so conflict between bernie and hillary is interesting.”
On July 14th, the GRU sent Wikileaks an encrypted email with the subject “Big Archive”, along with instructions on how Wikileaks can access its contents. Wikileaks later confirmed it had received the around 1 gigabyte file, and would make its contents available “Later this week”. Then, on July 22nd, they released over 20,000 emails and other documents. The Democratic National Convention was 3 days later.

On September 15th, DCLeaks DMed Wikileaks on twitter, asking, "Hi there! I'm from DCLeaks. How could we discuss some submission-related issues? I'm trying to reach out to you via your secured chat but getting no response. I've got something that might interest you. You won't be disappointed, I promise." Wikileaks replied, “Hi there”, but did not immediately get a response.
That same day, Guccifer2.0 messaged the DCLeaks account, the first contact between the personas. Guccifer informed DCLeaks that Wikileaks was attempting to contact DCLeaks.
On October 7, 2016, WikiLeaks released the first batch of Podesta emails. The release of the emails coincided with the scandalous Access Hollywood tape. WikiLeaks published 33 batches of stolen emails between October 7, 2016, and November 7, 2016, and over 50 thousand of Podesta’s emails.
When the DNC announced it had been hacked by Russian State actors, Assange made several public statements designed to obscure the origin of the materials. On August 9th, the Wikileaks twitter posted,
Then, in an interview on August 25th, Assange was asked about his focus on Seth Rich. He responded, "We're very interested in anything that might be a threat to alleged WikiLeaks sources."
The interviewer pressed Assange, asking if he was implying Rich was behind the leaks, who was then murdered. Assange replied,
Assange continued to play dumb when US Intelligence began announcing its certainty of Russian interference, desperately trying to hide the GRU source. Assange told Rep. Dana Rohrabacher the hack was an inside job, and that he had proof it wasn’t the Russians who gave him the information.

Seth Rich
The Trump Campaign began showing interest in Wikileaks’ releases as soon as they began releasing. In particular, campaign official Roger Stone showed significant interest. Stone began trying to contact Assange, would regularly brag to his coworkers about his access to him, and started making predictions on when and what the next releases would be. According to multiple witnesses, this began in June 2016 continuing through October 2016.
All the while, it was the Guccifer2.0 persona who initially contacted Roger Stone. Stone began telling members of the campaign that he was in contact with someone with Wikileaks access, and in August 2016, publicly protested against the Guccifer account getting banned on twitter. After it was reinstated, Stone received a message from the account, saying
"thank u for writing back... do u find anyt[h]ing interesting in the docs i posted?"
The next day, they added,
“please tell me if i can help u anyhow...it would be a great pleasure to me.”
Then, on September 9th, they messaged Stone again, asking
"what do u think of the info on the turnout model for the democrats entire presidential campaign."
Stone responded,
"[p]retty standard."
These are the only known communications between Guccifer2.0 and Roger Stone.
Though Stone initially publicly denied having any connections to Assange or Guccifer2.0, he later admitted he lied, and that he did have knowledge about the leaks prior to any public announcement from Wikileaks. According to Rick Gates, an associate of Stone’s, he told Gates something “big” was coming concerning an info leak. He told Gates that he thinks Assange has Clinton’s emails. When asked when the release would happen, Stone replied with “Soon”.
Stone also told Paul Manafort, another convicted campaign official, that he was dealing with someone in contact with Wikileaks. Campaign officials were lukewarm on Stone’s knowledge of these leaks, likely taking them with a grain of salt until the July 22nd release. Micheal Cohen remembered a time when Stone called Trump’s office with Cohen there sometime in July, telling them excitedly that the leaks were soon coming. Trump responded with something like “Oh, alright”, seeming disinterested. Later, when the files were released, Trump told Cohen,
“I guess Roger was right”.
After the release, Stone joined in a conference call with Manafort and Gates. According to Gate’s, Manafort congratulated Stone. Manafort also claimed that when he told Trump of this, Trump said Manafort should stay in touch with Stone. Manafort told this to Stone, then asked to keep him in the loop for any Wikileaks updates. By late summer 2016, the campaign was starting to plan press strategies and messaging around the leaks that were purported to happen.
Stone also spoke with Steve Bannon, chairman of the Trump campaign, about the leaks. According to Bannon, Stone had bragged to him on August 13th about his connection to Assange, and that he should consider Stone’s access.
On August 2, 2016, Jerome Corsi, a self described “operative” for Stone, sent Stone an email reading, in part,
“Word is friend in embassy plans 2 more dump ... Time to let more than Podesta to be exposed as in bed w[ith] enemy … That appears to be the game hackers are now about. Would not hurt to start suggesting HRC [Hillary Rodham Clinton] old, memory bad, has stroke ... I expect that much of next dump focus, setting stage for Foundation debacle.”

Roger Stone
Starting in August 2016, Roger Stone began communicating with Randy Credico about WikiLeaks. Credico, a New York radio host, interviewed Julian Assange on August 25, 2016. The next day, August 26, 2016, Credico texted Stone that Julian had mentioned him the previous night. When Stone asked what Assange had said, Credico assured him they hadn’t said anything bad about Stone.
The next day, he followed up,
“Julian Assange has kryptonite on Hillary.”
In September 2016, Stone asked Credico to request Assange for any emails from the State Department or candidate Clinton that pertained to Benghazi. Credico agreed.
Later, on October 1st, Credico message Stone, saying,
“big news Wednesday . . . now pretend u don’t know me . . . Hillary’s campaign will die this week.”
After a delay on a planned Oct 2 Wikileaks Press conference, Stone asked Credico if Assange had “backed off”.
“I think it’s on for tomorrow.” Credico replied. “Off the record, Hillary and her people are doing a full-court press to keep Assange from making the next dump… that’s all I can tell you on this line… Please leave my name out of it.”
Later, Credico would say he couldn’t remember why he made this claim.
Stone would keep repeating the Credico predictions throughout that week, and on October 7th, the scandalous Access Hollywood tape was released. Less than 1 hour later, Wikileaks released the Podesta emails, proving Stone right once again. Though the investigation sought to find if Stone had anything to do with the coincidence, much of the evidence was obstructed or unclear.

Randy Credico
Stone was not the only person who was in communication with Wikileaks. Donald Trump Jr received a message on September 20th, 2016,
“A PAC-run, anti-Trump site, putintrump.org, is about to launch. The PAC is a recycled pro-Iraq War PAC. We have guessed the password—it is ‘putintrump’. See ‘About’ for who is behind it. Any comments?”
Trump Jr then emailed a variety of campaign staff, saying
"Guys, I got a weird Twitter DM from WikiLeaks … Not sure if this is anything, but it seems like it’s really WikiLeaks contacting me … Do you know the people mentioned or what conspiracy they might be looking for? ... Let me know your thoughts and whether we want to look into it."
Jr attached a screenshot of the “About” page for the unlaunched site PutinTrump.org. The next day, he messaged Wikileaks back, saying
“Off the record, I don’t know who that is but I’ll ask around. Thanks.”
On October 3, 2016, WikiLeaks sent another direct message to Donald Trump Jr., requesting that “you guys” help share a link alleging that candidate Clinton had advocated using a drone to target Julian Assange.
Trump Jr. replied that he had already shared it and asked, “what’s behind this Wednesday leak I keep reading about?” WikiLeaks did not respond.
On October 12, 2016, WikiLeaks DMed him again, saying that it was
“great to see you and your dad talking about our publications. Strongly suggest your dad tweets this link if he mentions us wlsearch.tk.”
Two days later, Trump Jr. publicly tweeted the wlsearch.tk link.
Conclusion
The Mueller Report revealed a coordinated effort by the Russian government to undermine the democratic process. The GRU, Russia's military intelligence agency, conducted extensive cyberattacks against Democratic targets, including the Clinton Campaign, the DNC, and the DCCC. They exfiltrated sensitive data and disseminated it through online personas such as Guccifer 2.0 and DCLeaks, culminating in releases via WikiLeaks. The Trump Campaign exhibited interest in these releases, with Roger Stone serving as an intermediary between the campaign and WikiLeaks, claiming advance knowledge of forthcoming disclosures. While the investigation did not establish a criminal conspiracy between the Trump Campaign and Russia, the evidence was sufficient to support charges of computer intrusion and related offenses against GRU officers for their role in the election-related hacking activities.
In my next article, I will detail the extensive back and forth between Wikileaks, the GRU, and the Trump campaign, to fully detail the extent of their corroboration. Much of the evidence was obstructed, but what remains can paint a clear picture, even if not a picture which could be used in criminal court.